According to the recently released Microsoft Digital Defense Report, Ransomware attackers launched over 600 million attacks on Microsoft customers daily in the last year. This marks a 2.75 times increase in the attack attempts over the previous year. However, the good news is that the number of successful attacks involving data encryption and ransom demands has dropped three-fold. Advancements in automatic attack disruption technologies have, according to the Report, led to fewer Ransomware attacks reaching the encryption stage.
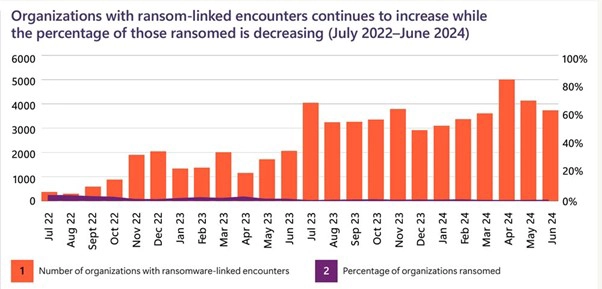
Source: Microsoft Defender for Endpoint
Evolving Types of Cyber Attacks
According to the Microsoft Report, Microsoft tracks more than 1500 unique threat groups, including more than 600 nation-state threat actor groups, 300 cybercrime groups, 200 influencer operation groups, and many others. The report also says that the top five ransomware families report, viz. Akira, Lockbit, Play, Blackcat, and Basta have accounted for 51% of the documented attacks.
The most common means the ransomware attackers employ include exploiting social engineering, identity compromises, as well as vulnerabilities in public-facing applications or even unpatched operating systems. Once the attackers are in the system, they would usually install remote monitoring tools or tamper with the security enablement present in the system.
The report also says that 70% of the successful ransomware attacks involved remote encryption and 92% of attacks targeted unmanaged devices. It also finds that the major types of attacks in the past year include:
- Infrastructure attacks
- Cyber-enabled financial fraud
- Attacks on e-Commerce spaces
- Impersonation
- Deepfakes
- Account takeover
- Identity and social engineering attacks
- Password theft attacks
- SIM swapping
- Help desk social engineering
- Credential phishing
- Phishing-as-a-Service attacks
- DDoS attacks
- Anti-virus tampering
- Tampering with security settings
Rising Nation-State Attacks
The Microsoft Report finds that both the financially motivated threat actors and nation-state actors are increasingly using the same information stealers and command-and-control frameworks. One thing that has changed, though, per the report, is that financially motivated actors are now using cloud identity compromise attacks which is a tactic that was earlier commonly used by nation-state attackers. The evolving methods being used by cybercriminals are blurring the lines between nation-state-backed malign activity and cybercriminal activity.
The major threat actor groups are from Russia, China, Iran, and North Korea. The report finds that these nation-states may be leveraging financial threat actors for profit or they could be conveniently ignoring the activities taking place within their borders.
Rising Incomes of Cyber Attackers
One important finding of the Microsoft report that is really shocking is the huge amounts of money that cyber attackers can make from the attacks. The report finds that the government as a sector makes up for only about 12% of the attackers’ target set, while most victims are private individuals or companies. The most targeted sectors include:
- IT
- Education
- Government
- Think tanks and NGOs
- Transportation
The successful attacks and the ransoms paid are rising. Plus, the attackers could often be sponsored by nation-states or involved with them, which also makes a source of income for them. Overall, the incomes of attackers are rising greatly and shockingly.
Generative AI On Both Sides
Both cyber attackers and defenders are now deploying Generative AI which is having a significant impact on cybersecurity. The Microsoft Report recommends limiting the usage of Generative AI as much as possible from a cybersecurity perspective, especially when handling sensitive data and data governance policy compliance. AI can have a major impact on the cybersecurity measures, such as:
- When attackers and defenders both use Generative AI, it is easy for information to get compromised
- Nation-state actors can use Generative AI to generate deceptive audio and videos
- AI is being used to drive phishing, resume swarming, and deepfake attacks
- Limiting foreign influence operations is no longer a useful measure for keeping things in check
- Having stringent AI policies and principles in the company can help mitigate some risk that comes with using AI tools
- Different authorities approach information and AI security in different ways, though generally, everyone recognizes the importance of security in the development of AI
Preventing Common Cyberattacks
Since cyberattacks are becoming so prevalent and increasingly expensive & dangerous, what can enterprises as well as individuals do to prevent becoming victims of common cyberattacks?
Here are some things enterprises can do, as suggested by the Microsoft Report:
- Implement policies like multi-factor authentication & attack-surface reduction which would help disrupt the attacks at the technique layer
- ‘Secure-by-default’ should be a default setting for everything, even if not very well-received by employees
- Get your company’s password game to be the strongest
- Pre-configured security settings should be tested regularly, including security defaults and managed Conditional Access Policies, including in the Report-Only mode, so the company can prepare for potential impact before it becomes a real impact
- Sensitive data should be classified and labeled so
- High-risk data and high-risk users should have DLP, data lifecycle, as well as Conditional Access Policies around them

Get CISSP certification with Cognixia.
Once you have employees with the CISSP certification, they will demonstrate their skills to benefit your business with –
- Complete understanding of how to secure or protect confidential business data from hackers.
- Analyze risks and be aware of the common hacker strategies that can affect your business. They can determine the weak points of the organizations and work on them.
- Aptitude in improving customer and employee privacy, ensuring all the information stays with the business only.
Get (ISC)2 CISSP Online Training & Certification and increase your business visibility as well as credibility in the cybersecurity market. Cognixia is the world’s leading digital talent transformation company that offers a wide range of courses, including CISSP training online with a comprehensive CISSP study guide.
Here’s what you will cover in this course –
- Learn and apply the concepts of security & risk management
- Gain an understanding of security engineering to protect information by exploring and examining security models and frameworks
- Learn how to identify, categorize, & prioritize assets
- Examination and security network architecture and its components
- Learn how to identify & control access to protect assets
- Designing and conducting security assessment strategies, logging, & monitoring activities
- Developing a recovery strategy and maintaining operational resilience
- Learn how to secure the software development cycle
Prerequisites
- Candidates for the CISSP certification should have at least 5 years of total paid work experience in two or more of the 8 CISSP CBK domains. Any extra certificate from the (ISC)2 authorized list, a four-year college degree, or a regional equivalent would qualify as one year of the necessary experience.
- If a candidate doesn’t have enough experience to qualify as a CISSP, they can still become an Associate of (ISC)2 by completing the CISSP test. After that, they will have 6 years to acquire the 5 years of necessary experience.

